Ballast
Insights
Read Ballast’s best-practice case studies, real-time alerts and after-action reviews to keep you up to date with IT and security trends.
- All
- Secure Managed Services
- News
- Press Release
- Professional Services
- Advisory Services
- Critical Cyber Alert

Cyber criminals use legitimate IT RMM tools to control computers
January 26, 2023
Remote Management and Monitoring (RMM) are commonly used by IT professionals to remotely access and manage computers. However, cyber criminals have found ways to exploit these tools, using them to gain access to a computer to install malware and discover and exfiltrate data.
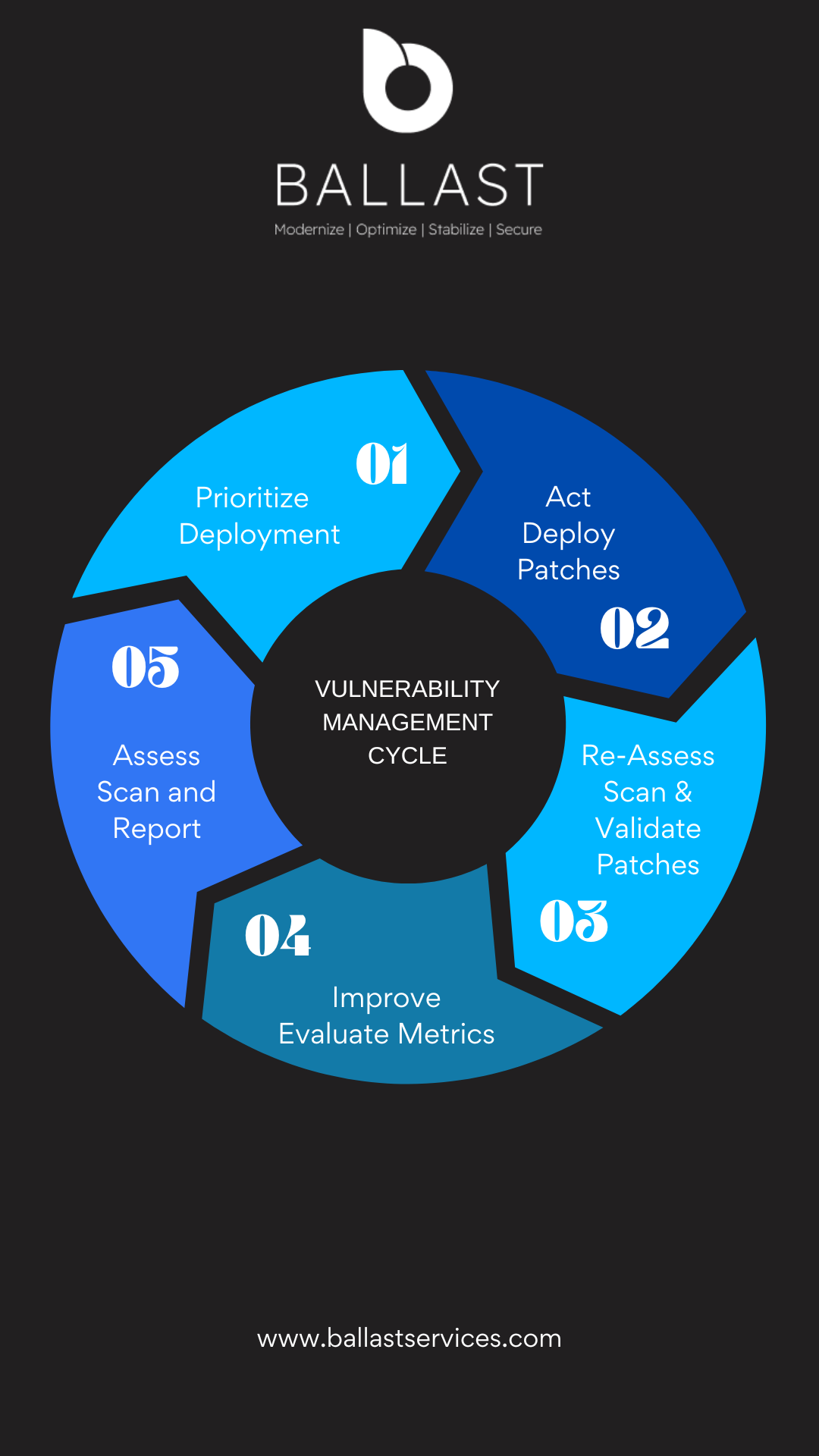
Patch Management is a Critical Component of Cybersecurity
January 25, 2023
Your organization depends on your information technology stack to operate your business and store sensitive information. As a result, the risk of cyber-attacks such as ransomware and data breaches potentially crippling your business has increased significantly. One of the most effective ways to mitigate these risks is through the implementation of a comprehensive patch management strategy.

Why You Need Regular Risk Assessments for Disaster Recovery and Business Continuity
January 11, 2023
Disaster Recovery (DR) and Business Continuity (BC) planning are essential for any organization, as they help ensure that the company can continue to operate in the event of a disaster. However, to develop an effective disaster recovery and business continuity plan, it is critical to conduct a risk assessment on an annual basis to understand your business risk as your business changes and cyber risks grow in type and complexity.

Cyber Insurance has become a Conundrum
January 06, 2023
Cybersecurity is a critical concern for organizations of all sizes, and cyber insurance can provide financial protection in the event of a cyber-attack. However, many organizations may find it challenging to get affordable cyber insurance with premiums skyrocketing in cost and with ever-changing requirements to get or keep a policy. Managed security services can make it easier for organizations to get cyber insurance by helping to reduce their cybersecurity risk.

Speed Matters when Protecting Companies from Cyber Attacks
January 04, 2023
Technology is constantly evolving and companies must adapt to stay competitive. Unfortunately, with each change comes the risk of introducing vulnerabilities and new attack surfaces. Cybercriminals are always on the lookout for these vulnerabilities, and they're not wasting any time exploiting them with increased use of vulnerabilities becoming a trend in 2022. That's why speed matters when it comes to protecting companies from cybercriminals.
Secure Backups Can Save Your Company
December 14, 2022
It’s 2023 and cybercrime is a growing concern for organizations of all sizes. A single cyber-attack can cause significant financial loss, damage to reputation, and a loss of sensitive information. One of the most effective ways to protect against such attacks is to have secure backups in place.

The Importance of Endpoint Detection and Response (EDR) for Cyber Security Insurance
December 09, 2022
EDR is a vital tool for businesses looking to secure their networks and data. It provides a proactive approach to cyber security, detecting and responding to potential threats. Additionally, it is a requirement for many cyber security insurance policies, providing insurance providers with the necessary information to assess the risk of a cyber attack and determine the appropriate level of coverage.

How ITIL-based Change Management Helps Organizations Stay Secure
December 01, 2022
ITIL, or Information Technology Infrastructure Library, is a framework for IT service management that provides a structured approach to managing IT services. One of the core components of ITIL is Change Management, which is a process for managing and controlling changes to IT services.

Firewall Management is a Must-Have for Retail
November 04, 2022
When you think of retail businesses, you probably think of customer service, sales, and stocking the shelves. But did you know that cyber security is just as important? With the rise of e-commerce and the increased use of technology in the retail industry, it's more crucial than ever to protect your business from cyber threats. And one of the most important ways to do that is through firewall management.
Let's Get
Started
We help keep your company, end users and data protected.
Connect with us to learn more about how we can help you modernize, optimize, stabilize and secure your technology investments.
